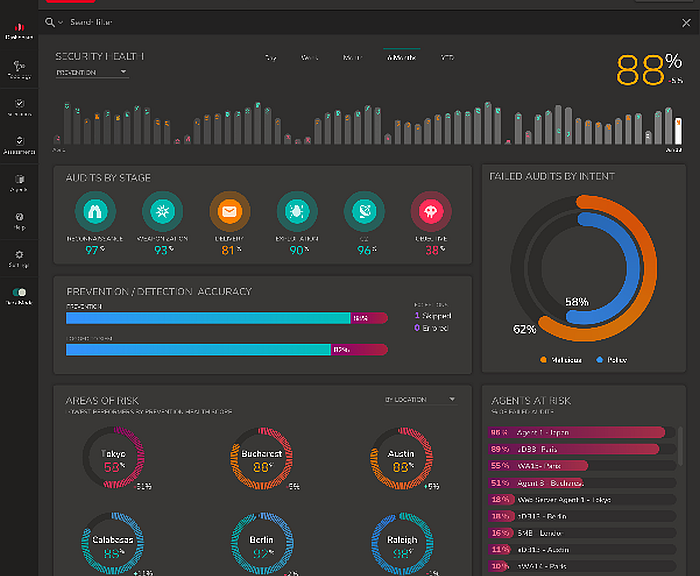
- In the 2021 edition of its Computer Network Security Report, Keysight Technologies presents the trends observed over the past year by its Application and Threat Intelligence (ATI) research center.
The top threats include phishing, ransomware and supply chain breaches.
“This report combines the lessons learned from 2020 with useful insights for network security professionals for 2021. Both the data and insights are based on research conducted by our Application and Threat Intelligence (ATI) research center,” said Scott Register, senior vice president of security solutions at Keysight. “Cybercrime did not take a vacation during the pandemic. Cybercriminals exploited phishing, ransomware and supply chain vector attacks to hit networks for financial gain. We expect these network security trends to continue in 2021.”
Phishing attacks increased by 62 percent in 2020 compared to 2019.
Financial gain is the primary motivation for cybercriminals. Ransomware deployment saw a sharp increase from June 2020. While this trend was seen across all industries, healthcare was particularly affected. 59 percent of attacks occurred in the second half of 2020.
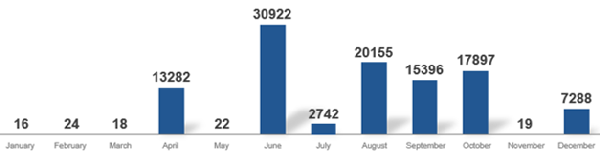
According to Keysight’s experts, the supply chain remains a weak point for companies, and the SolarWinds hack, which targeted the U.S. government, its federal agencies and several other private companies in 2020, is one example. The SolarWinds attack reinforced the need for security architects to take a complete holistic approach.
An enterprise’s supply chain is not limited to its devices. It consists of all the external entities that provide a company with software and hardware components and supplies needed to manufacture a product.
The supply chain, which is critical to the operation of a business, involves many players: utilities, couriers, suppliers, etc. Network security must take into account the interactions with all of these partners who may have access to or exchange information with its IT systems.
To increase the level of security, it is important to ensure that systems and users can only access the internal or external resources they absolutely need. Organizations must also implement solutions that provide visibility into their networks and cloud resources so that network security teams can spot anomalies and potential breaches that could lead to malicious intrusions.