- Keysight Technologies and Synopsys have teamed up to provide a cybersecurity assessment solution to ensure that IoT devices are protected as they enter the market.
- As part of the agreement, Synopsys’ Defensics tool for Fuzz testing will be optionally integrated into Keysight’s IoT security assessment solution.
The global market for IoT devices is recording clear growth. It is expected to reach $413.7 billion by 2031. But, according to Palo Alto Networks’ IoT Threat Report, IoT devices are vulnerable targets. 57% of IoT devices are said to be at risk of medium or high severity attacks.
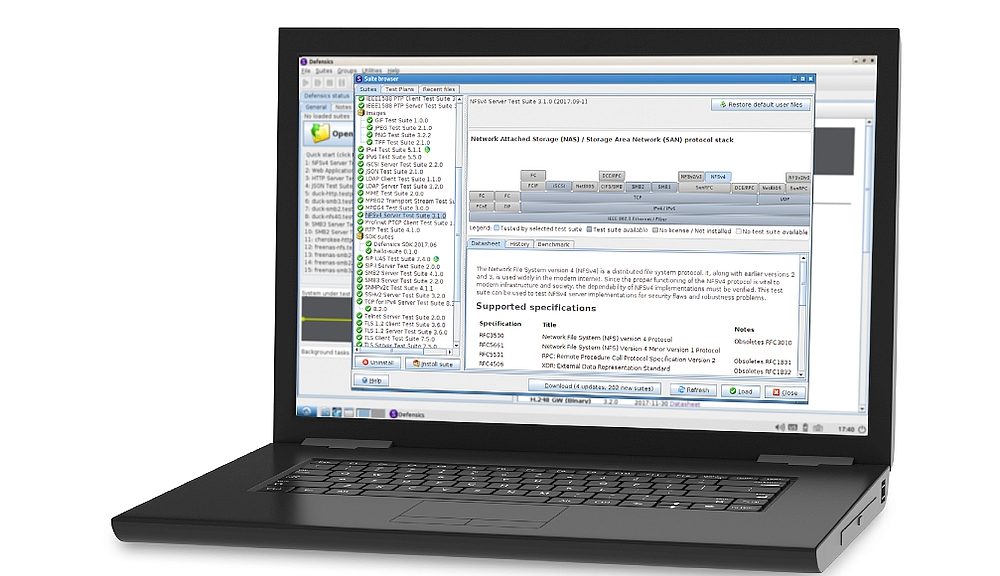
Faced with the proliferation of IoT devices and cyberattacks, device manufacturers need assessment tools to identify and remediate device security vulnerabilities. Synopsys’ Defensics fuzzing test tool has been designed to detect security flaws in IoT devices. Fuzz testing is an automatic software testing technique that injects invalid, malformed or unexpected data into a device to reveal flaws and vulnerabilities.
The Defensics tool is capable of analyzing over 300 technology protocols used in various industries to test for unknown vulnerabilities and weaknesses. In addition to reporting security flaws discovered through fuzzing, the solution detects potential exploits resulting from weak authentication and encryption, expired certificates, Android vulnerabilities and Android Debug Bridge (ADB) exposures, known common vulnerabilities and exposures (CVEs), and flaws embedded in protocol stacks, such as Bluetooth Low Energy attacks like Sweyntooth and Braktooth.
In addition, the Keysight IoT Security Assessment solution enables IoT devices to be tested and awarded the new White House Cyber Trust Mark certification when it is launched. This turnkey cybersecurity certification platform enables automated validation via a point-and-click interface.
“With Synopsys’ fuzzing tool, Keysight can provide device manufacturers with a complete security testing solution to identify previously unknown protocol stack vulnerabilities in their devices while evaluating them for known threats, from a single interface,” points out Ram Periakaruppan, vice president and general manager of network test and security solutions, Keysight.